- 注目検索ワード
本記事は2014年10月2日に配信した、 「[DEF CON 22 レポート] SECTF 競技レポート」 の英語版です。
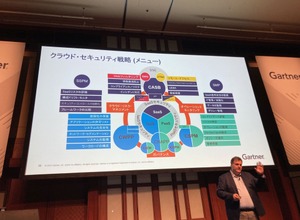
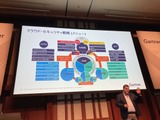
最後に、ハンキンス氏はクラウドセキュリティ全体像を戦略メニューとして図示した。上記で説明したソリューションやツール、各種フレームワークやプラットフォームが、機能や用途ごとに俯瞰できるものだ。この図は、ガートナーのクラウドセキュリティのコンサルティングの戦略ベースを示したものといってもよい。自社のセキュアクラウドを構築するときの「レシピ」として利用することができるだろう。
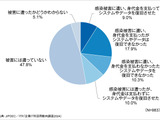
幸いなことに、これらの履歴書の情報はほとんどの場合少なくとも 10 年前のものだが、それでも個人情報が多く含まれていることには変わりない。
大英図書館には多くの個性がある。独特の複雑な役割分担があり、それは法律で独自に規制されている。別の見方をすれば、ITインフラストラクチャは古くから確立されたコアサービスとの間でリソースを奪い合い、しばしば失敗するという点で、国やその他の大規模な組織の典型である。大英図書館の状況も、うまくいかないことの壮大な例にすぎない。
興味深い研究発表として、イスラエル工科大学やコーネル工科大学などの研究者は、OpenAI の ChatGPT や Google の Gemini など、生成 AI を活用する AI アプリケーションを標的としたゼロクリックワーム「Morris II」を開発し、ユーザーの個人情報の窃取に成功したことを発表しました。



















![人気連載 Scan PREMIUM Monthly Executive Summary の岩{丼}先生の著作にサインいただきました [Scan PREMIUM 創刊25周年記念キャンペーン 読者特典] 画像](/imgs/std_m/43329.jpg)



